
A SOP Template for Managed IT Services provides a structured framework for streamlining IT support processes and ensuring consistent service delivery. It outlines key procedures, roles, and responsibilities to maintain system reliability and security. This template helps organizations achieve operational efficiency and meet compliance standards effectively.
Client Onboarding and Documentation Process.
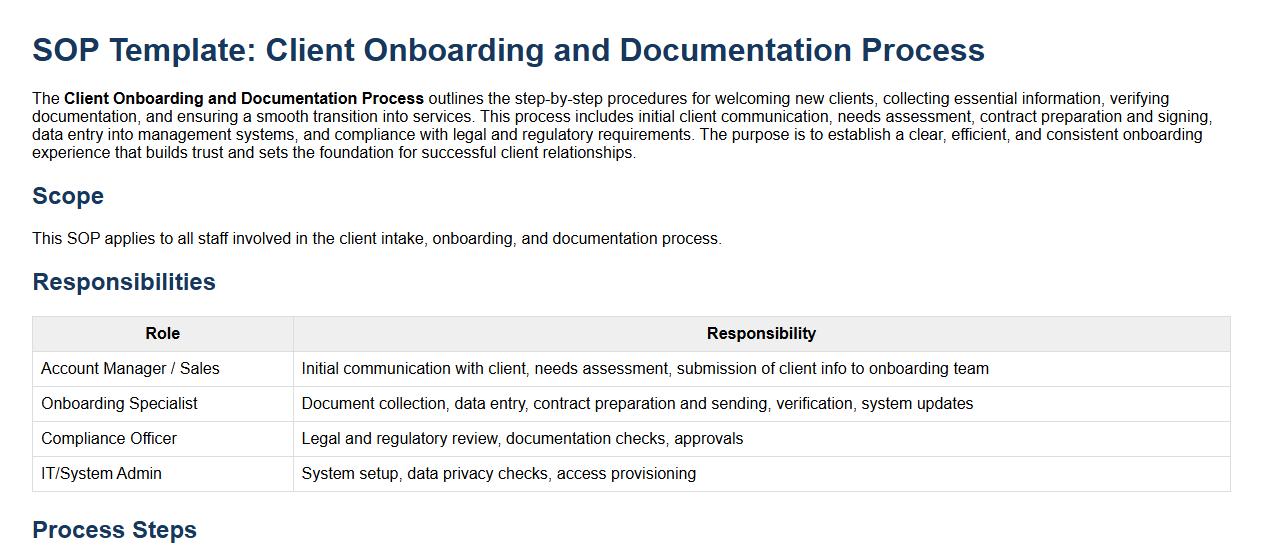
The Client Onboarding and Documentation Process outlines the step-by-step procedures for welcoming new clients, collecting essential information, verifying documentation, and ensuring a smooth transition into services. This process includes initial client communication, needs assessment, contract preparation and signing, data entry into management systems, and compliance with legal and regulatory requirements. The purpose is to establish a clear, efficient, and consistent onboarding experience that builds trust and sets the foundation for successful client relationships.
Service Level Agreement (SLA) Management.

This SOP defines the processes for effective Service Level Agreement (SLA) Management, including SLA creation, monitoring, performance measurement, issue escalation, and regular review. The goal is to ensure that service commitments between providers and clients are clearly documented, consistently met, and continuously improved to maintain high customer satisfaction and operational efficiency.
Incident Ticketing and Resolution Workflow.
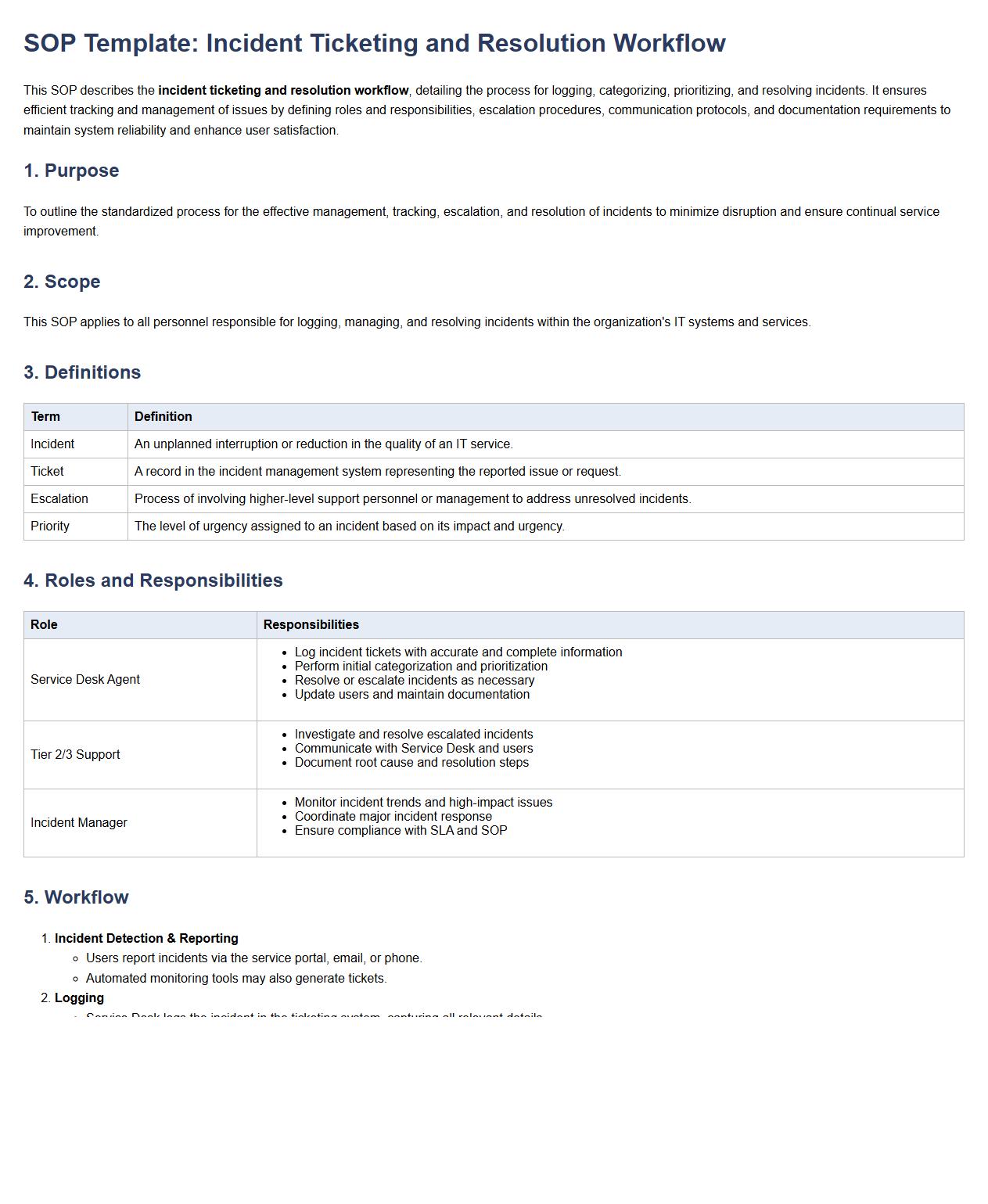
This SOP describes the incident ticketing and resolution workflow, detailing the process for logging, categorizing, prioritizing, and resolving incidents. It ensures efficient tracking and management of issues by defining roles and responsibilities, escalation procedures, communication protocols, and documentation requirements to maintain system reliability and enhance user satisfaction.
Change Management Procedures.
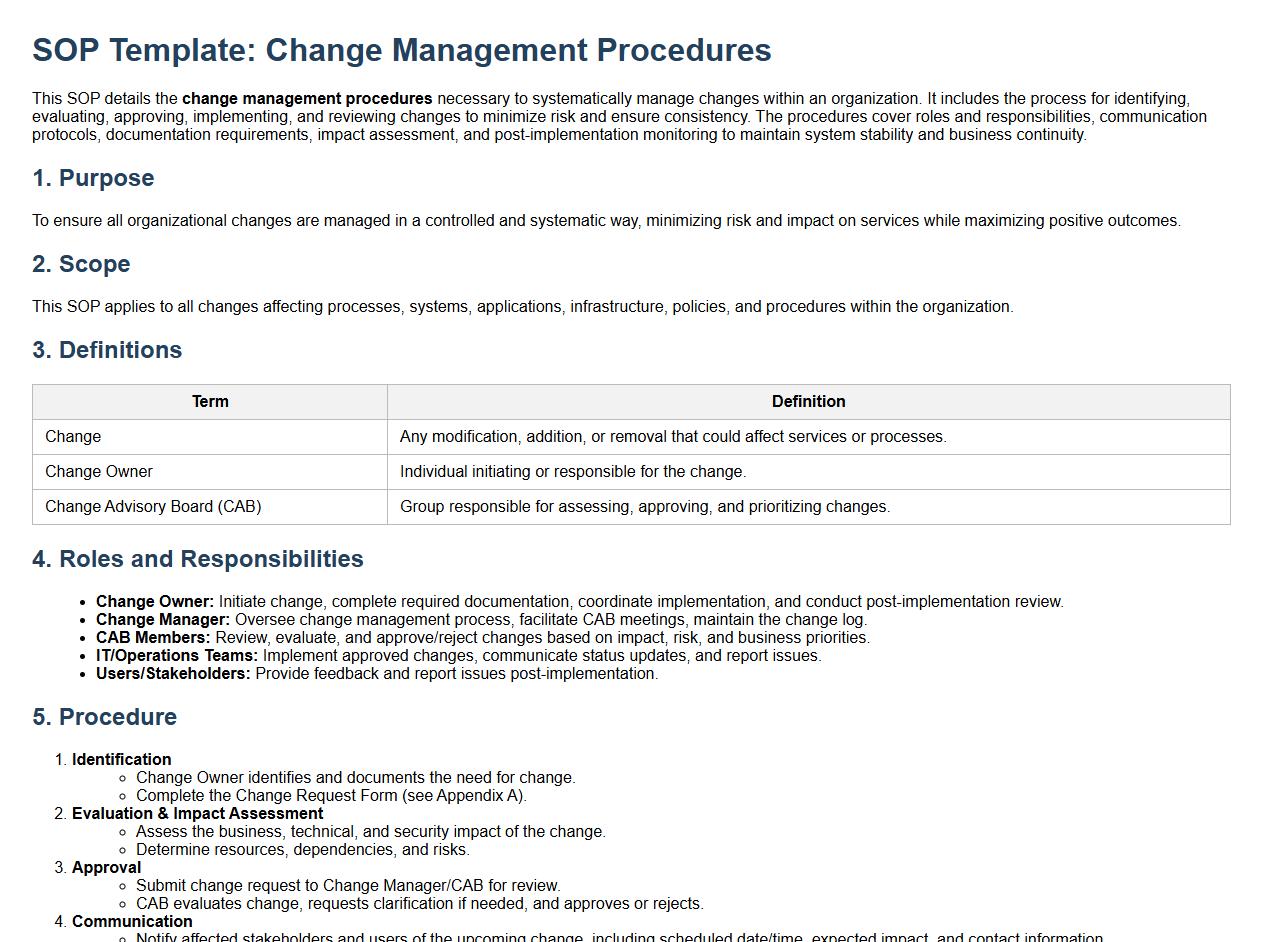
This SOP details the change management procedures necessary to systematically manage changes within an organization. It includes the process for identifying, evaluating, approving, implementing, and reviewing changes to minimize risk and ensure consistency. The procedures cover roles and responsibilities, communication protocols, documentation requirements, impact assessment, and post-implementation monitoring to maintain system stability and business continuity.
Remote Monitoring and Management (RMM) Protocols.

This SOP details the Remote Monitoring and Management (RMM) Protocols, encompassing procedures for continuous system monitoring, proactive issue detection, automated maintenance tasks, security management, and incident response. The protocols aim to ensure optimal performance, security, and reliability of IT assets through remote access and control, minimizing downtime and enhancing operational efficiency.
Patch Management and Software Updates Schedule.
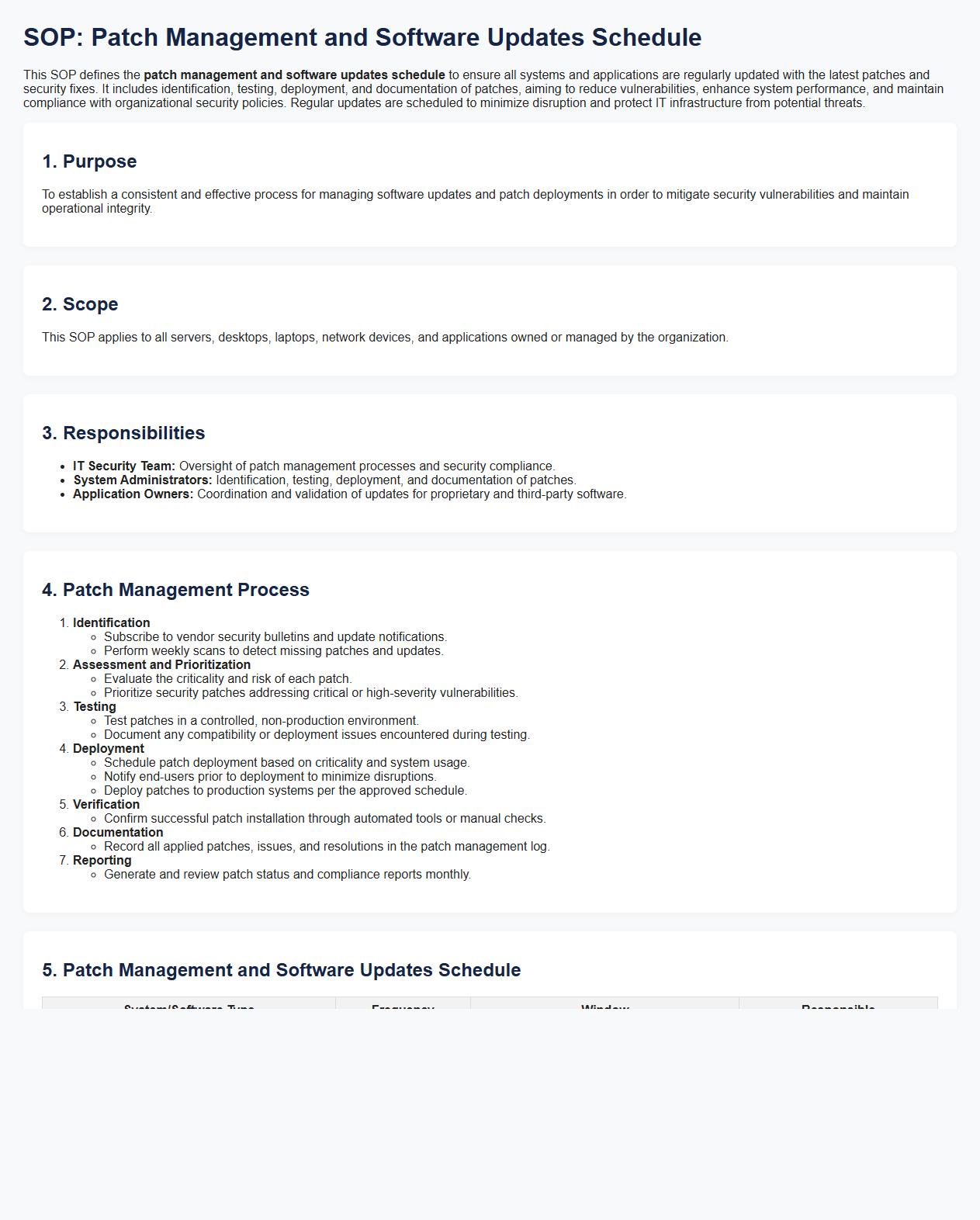
This SOP defines the patch management and software updates schedule to ensure all systems and applications are regularly updated with the latest patches and security fixes. It includes identification, testing, deployment, and documentation of patches, aiming to reduce vulnerabilities, enhance system performance, and maintain compliance with organizational security policies. Regular updates are scheduled to minimize disruption and protect IT infrastructure from potential threats.
Data Backup and Disaster Recovery Procedures.
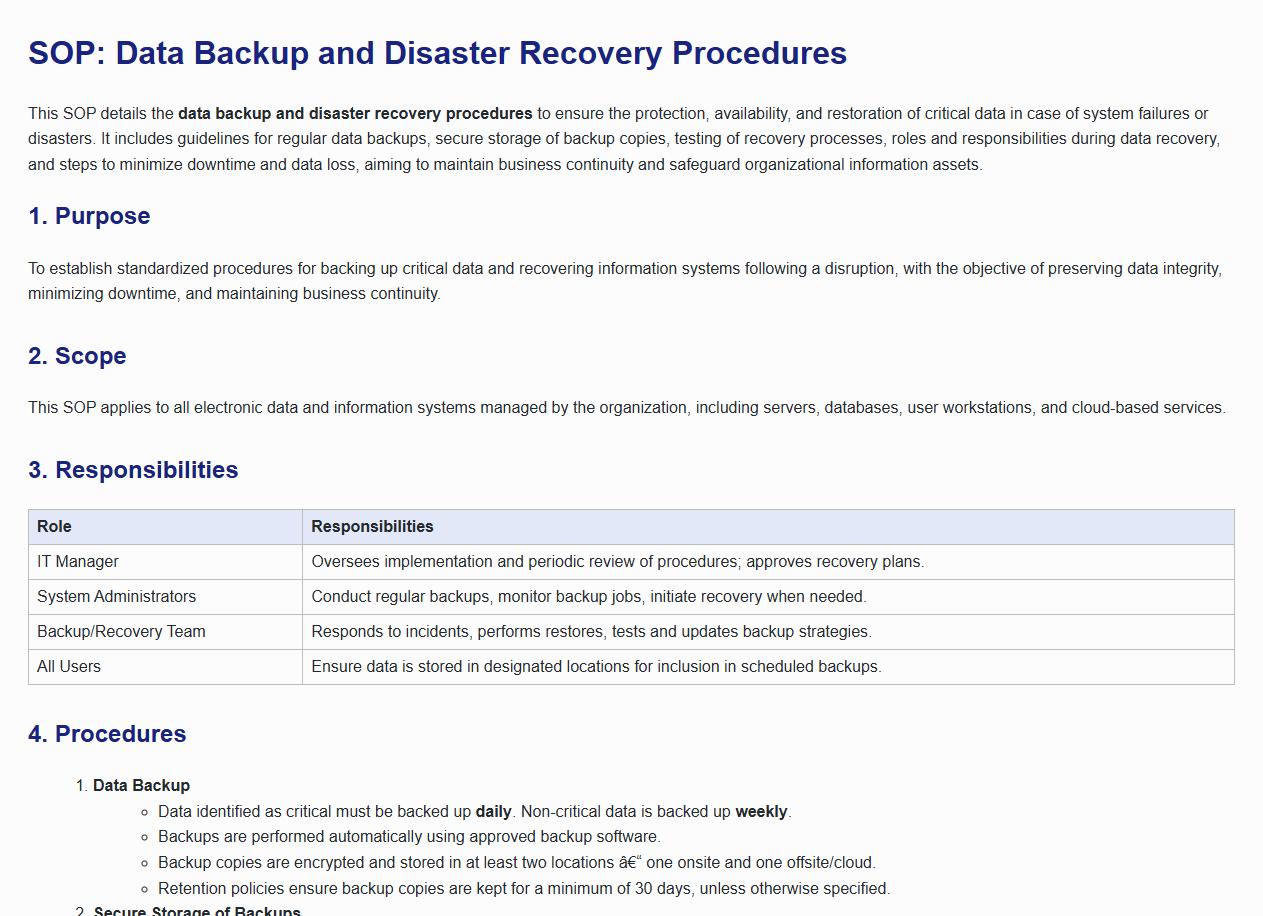
This SOP details the data backup and disaster recovery procedures to ensure the protection, availability, and restoration of critical data in case of system failures or disasters. It includes guidelines for regular data backups, secure storage of backup copies, testing of recovery processes, roles and responsibilities during data recovery, and steps to minimize downtime and data loss, aiming to maintain business continuity and safeguard organizational information assets.
User Access and Security Management.
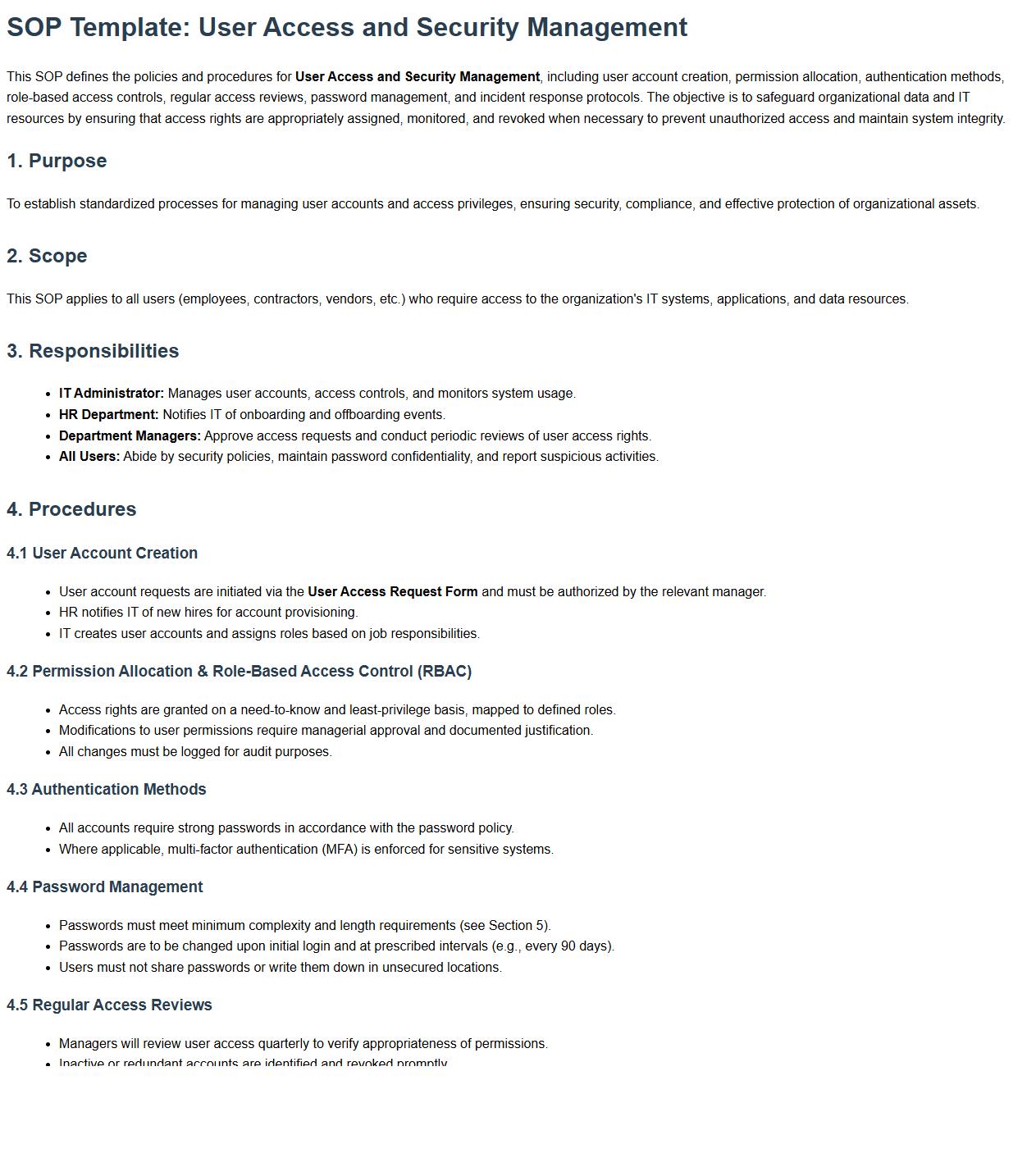
This SOP defines the policies and procedures for User Access and Security Management, including user account creation, permission allocation, authentication methods, role-based access controls, regular access reviews, password management, and incident response protocols. The objective is to safeguard organizational data and IT resources by ensuring that access rights are appropriately assigned, monitored, and revoked when necessary to prevent unauthorized access and maintain system integrity.
Hardware and Software Inventory Management.

This SOP defines the process for hardware and software inventory management, encompassing the tracking, recording, and maintenance of all IT assets, including computers, peripherals, and software licenses. It ensures accurate documentation, compliance with licensing agreements, timely updates, and effective resource allocation to optimize IT infrastructure and support organizational efficiency.
Offboarding and Account Termination Process.
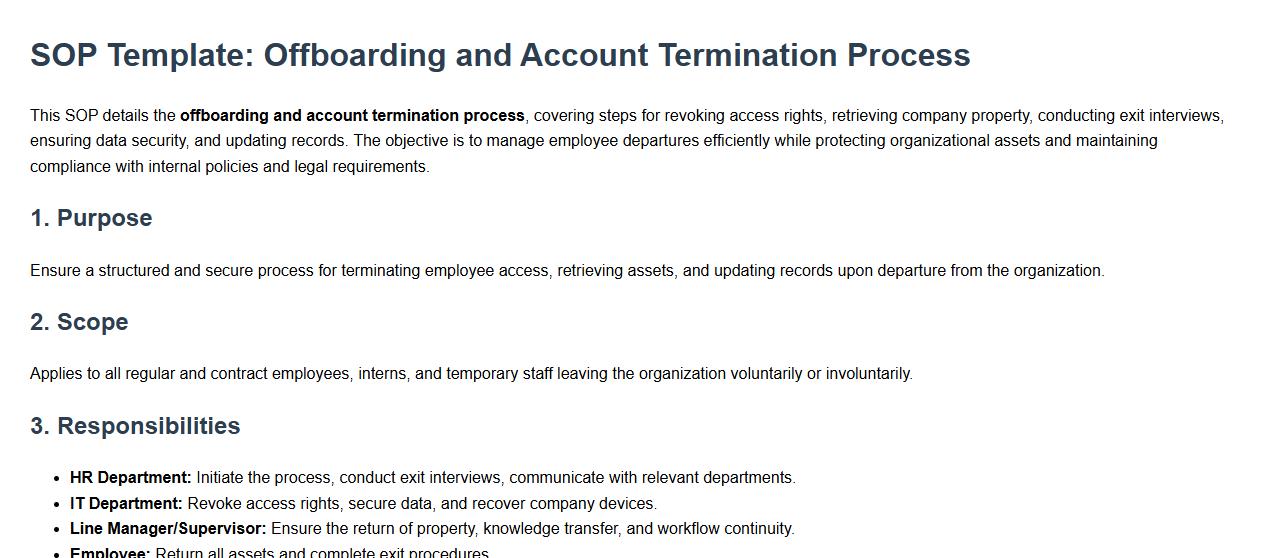
This SOP details the offboarding and account termination process, covering steps for revoking access rights, retrieving company property, conducting exit interviews, ensuring data security, and updating records. The objective is to manage employee departures efficiently while protecting organizational assets and maintaining compliance with internal policies and legal requirements.
What are the key objectives outlined in the SOP for Managed IT Services?
The SOP for Managed IT Services primarily focuses on ensuring consistent service delivery and operational efficiency. It aims to minimize downtime and enhance system reliability through structured processes. Furthermore, the SOP outlines objectives related to maintaining customer satisfaction by delivering timely and effective IT solutions.
Which stakeholders are responsible for the implementation of the procedures in the SOP?
The key stakeholders responsible include the IT service managers, technical support teams, and system administrators. These stakeholders ensure adherence to the SOP by actively managing daily operations and escalations. Additionally, the engagement of senior management is vital for resource allocation and oversight.
How does the SOP define the escalation process for unresolved IT incidents?
The SOP establishes a tiered escalation process beginning with frontline support and progressing to specialized teams if issues remain unresolved. Each escalation step has defined response times and documentation requirements. This process ensures that critical incidents receive prompt attention to minimize operational impact.
What are the standard metrics used for measuring compliance with the SOP?
Compliance is typically measured using service level agreements (SLAs), incident resolution times, and customer feedback scores. Regular audits and performance reviews help assess adherence to the SOP standards. These metrics provide clear benchmarks for continuous improvement.
Which security protocols must be adhered to as per the Managed IT Services SOP?
The SOP mandates strict adherence to protocols such as data encryption, multi-factor authentication, and periodic security audits. It also emphasizes compliance with industry regulations and company-specific policies. These measures are critical to safeguarding sensitive information and maintaining system integrity.
